LDAP認証
作成中です - Mitsuhiro Yoshida 2006年12月13日 (水) 17:41 (CST)
このドキュメントは、MoodleのLDAP認証をセットアップする方法に関して記述したものです。基本シナリオでは、すべてをシンプルかつ単刀直入に説明していますので、ほとんどのインストールの場合、十分な内容になっています。あなたのインストールが若干大規模で、複数のLDAPサーバまたはユーザのためにLDAPツリーで複数のロケーション (コンテクスト) を使用している場合、高度なシナリオをご覧ください。
基本シナリオ
前提
- あなたのMoodleサイトは、http://your.moodle.site/ にあります。
- あなたのPHPにはLDAPエクステンションが含まれています。LDAPエクステンションは有効かつロードされ、 ユーザ'admin'でログインした場合、 http://your.moodle.site/admin/phpinfo.php' に表示されます。
- あなたのLDAPサーバのIPアドレスは、192.168.1.100 です。
- あなたは、SSLで保護されたLDAP (LDAPS) を使用していません。この場合、特定のオペレーション (例 MS Active Directoryを使用してデータを更新できません -- 以後MS-AD --) は動作しませんが、ユーザ認証だけでしたらOKです。
- あなたは、ユーザの最初のログイン時にパスワードを変更させたくありません。
- MS-ADを使用している場合、あなたは認証データのソースとしてシングルドメインを使用しています (詳細は付録をご覧ください)。
- あなたは、LDAPツリーのルートとしてトップレベル識別名 dc=my,dc=organization,dc=domain を使用しています。
- あなたは、管理者権限のないLDAPユーザアカウントを持ち、LDAPサーバにバインドします。これは、特定のLDAPサーバでは必要ありませんが、MS-ADでは必要とします。あなたのLDAPサーバに匿名バインドを許可する設定がなされていても、LDAPユーザアカウントを使用することで問題が生じることはありません。このアカウントとパスワードが有効期限切れにならないことを確認して、可能な限り強固なパスワードを設定してください。Moodleの設定時、1度だけこのパスワードを入力する必要があります。ですから、可能な限り推測できないパスワードを作成することを恐れないでください。つまり、このユーザは、DN (識別名 Distinguished Name) cn=ldap-user,dc=my,dc=organization,dc=domain およびパスワード hardtoguesspassword を持ちます。
- あなたのすべてのMoodleユーザは、root直下にある moodleusers と呼ばれるOU (組織単位 organizational unit) に入ります。このOUは、DN ou=moodleusers,dc=my,dc=organization,dc=domain を持ちます。
- あなたは、LDAPユーザのパスワードをMoodleに保存したくありません。
Moodle認証の設定
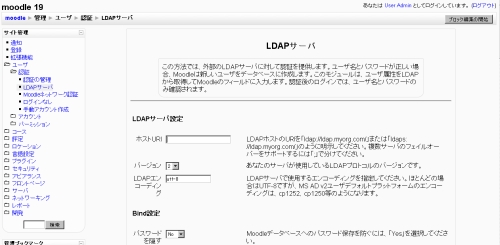
管理者としてログインして、管理 >> ユーザ >> 認証オプション へ移動してください。「認証方法の選択」リストボックスで、「LDAPサーバを使用する」を選択してください。次のようなページが表示されます:
さて、値を入力する必要があります。一歩一歩進みましょう。
| フィールド名 | 入力値 |
|---|---|
| ldap_host_url | あなたのLDAPサーバのIPアドレスが 192.168.1.100の場合、"ldap://192.168.1.100" と入力してください (引用符なし)。 |
| ldap_version | 本当に古いLDAPサーバを使用していない限り、version 3を選択してください。 |
| ldap_preventpassindb | あなたがMoodleデータベースにユーザパスワードを保存したくない場合、「Yes」を選択してください。 |
| ldap_bind_dn | 上記で定義されたバインドユーザの識別名です。cn=ldap-user,dc=my,dc=organization,dc=domain と入力してください。 |
| ldap_bind_pw | 上記で定義されたバインドユーザのパスワードです。hardtoguesspassword と入力してください。 |
| ldap_user_type | 選択:
|
| ldap_contexts | あなたのすべてのMoodleユーザは、コンテクスト (コンテナ) のDNで探されます。ここでは、ou=moodleusers,dc=my,dc=organization,dc=domain と入力してください。 |
| ldap_search_sub | ou=moodleusers,dc=my,dc=organization,dc=domain 配下にサブ組織単位 (sub organizational unit サブコンテクスト) があり、あなたがサブ組織単位をMoodleに検索して欲しい場合、yesを選択してください。そうでない場合、noを選択してください。 |
| ldap_opt_deref | しばしば、LDAPサーバはあなたが探している真の値が他のLDAPツリーにあると伝えるでしょう (これはエイリアスと呼ばれます)。あなたがMoodleに修飾参照を求めて、真の値をオリジナルロケーションから取得したい場合、「Yes」を選択してください。Moodleに修飾参照を求めない場合、「No」を選択してください。あなたが、MS-ADを使用している場合、「No」を選択してください。 |
| ldap_user_attribute | この属性は、あなたのLDAPツリーでユーザに名前をつける/検索するために使用されます。このオプションは、あなたが上記で選択した ldap_user_type の値から初期値を取得します。ですから、特別なことをすること以外、ここに値を入力する必要はありません。
By the way, it's usually cn (Novell eDirectory and MS-AD) or uid (RFC-2037, RFC-2037bis and SAMBA 3.x LDAP extension), but if you are using MS-AD you could use sAMAccountName (the pre-Windows 2000 logon account name) if you need too. |
| ldap_memberattribute | The attribute used to list the members of a given group. This option takes a default value based on the ldap_user_type value you choosed above. So unless you need something special, you don't need to fill this in.
By the way, the usual values are member and memberUid. |
| ldap_objectclass | The type of LDAP object used to search for users. This option takes a default value based on the ldap_user_type value you choosed above. So unless you need something special, you don't need to fill this in.
Here are the default values for each of the ldap_user_type values:
|
| Force change password | Set this to Yes if you want to force your users to change their password on the first login into Moodle. Otherwise, set this to no. Bear in mind the password they are forced to change is the one stored in your LDAP server.
As you don't want your users to change their passwords in their first login, leave this set to No |
| Use standard Change Password Page |
Bear in mind that changing your LDAP passwords from Moodle might require a LDAPS connection (this is true at least for MS-AD). Also, code for changing passwords from Moodle for anything but Novell eDirectory is almost not tested, so this may or may not work for other LDAP servers. |
| ldap_expiration |
Current code only deals with Novell eDirectory LDAP server, but there is a patch floating around to make it work with MS-AD too (search in the authentication forum). So unless you have Novell eDirectory server (or use the patch), choose No here. |
| ldap_expiration_warning | This value sets how many days in advance of password expiration the user is warned that her password is about to expire. |
| ldap_exprireattr | The LDAP user attribute used to check password expiration. This option takes a default value based on the ldap_user_type value you choosed above. So unless you need something special, you don't need to fill this in. |
| ldap_gracelogins | This setting is specific to Novell eDirectory. If set to Yes, enable LDAP gracelogin support. After password has expired the user can login until gracelogin count is 0.
So unless you have Novell eDirectory server and want to allow gracelogin support, choose No here. |
| ldap_graceattr | This setting is currently not used in the code (and is specific to Novell eDirectory).
So you don't need to fill this in. |
| ldap_create_context | |
| ldap_creators | The DN of the group that contains all of your Moodle creators. This is typically a posixGroup with a "memberUid" attribute for each user you want to be a creator. If your group is called creators, type cn=creators,ou=moodleusers,dc=my,dc=organization,dc=domain here. Each memberUid attribute contains the CN of a user who is authorized to be a creator. Do not use the user's full DN (e.g., not memberUid: cn=JoeTeacher,ou=moodleusers,dc-my,dc=organizations,dc=domain, but rather memberUid: JoeTeacher).
In eDirectory, the objectClass for a group is (by default) not posixGroup but groupOfNames, whose member attribute is member, not memberUid, and whose value is the full DN of the user in question. Although you can probably modify Moodle's code to use this field, a better solution is just to add a new objectClass attribute of posixGroup to your creators group and put the CNs for each creator in a memberUid attribute. In MS Active Directory, you will need to create a security group for your creators to be part of and then add them all. If your ldap context above is 'ou=staff,dc=my,dc=org' then your group should then be 'cn=creators,ou=staff,dc=my,dc=org'. If some of the users are from other contexts and have been added to the same security group, you'll have to add these as separate contexts after the first one using the same format. |
| First name | The name of the attribute that holds the first name of your users in your LDAP server. This is usually givenName.
この設定は任意です。 |
| Surname | The name of the attribute that holds the surname of your users in your LDAP server. This is usually sn.
この設定は任意です。 |
| Email address | The name of the attribute that holds the email address of your users in your LDAP server. This is usually mail.
この設定は任意です。 |
| Phone 1 | The name of the attribute that holds the telephone number of your users in your LDAP server. This is usually telephoneNumber.
この設定は任意です。 |
| Phone 2 | The name of the attribute that holds an additional telephone number of your users in your LDAP server. This can be homePhone, mobile, pager, facsimileTelephoneNumber or even others.
この設定は任意です。 |
| Department | The name of the attribute that holds the department name of your users in your LDAP server. This is usully departmentNumber (for posixAccount and maybe eDirectory) or department (for MS-AD).
この設定は任意です。 |
| Address | この属性の名称は、あなたのLDAPサーバでユーザの所在地住所 (番地) を保持します。これは通常、streetAddress または street' です。
この設定は任意です。 |
| City/town | この属性の名称は、あなたのLDAPサーバで、ユーザの所在地住所 ( 市/町 ) を保持します。これは通常、l (小文字のL) または localityName (MS-ADでは有効ではありません) です。
この設定は任意です。 |
| Country | この属性の名称は、あなたのLDAPサーバで、ユーザの所在地住所 ( 国 ) を保持します。これは通常、c' または countryName (MS-ADでは有効ではありません) です。
この設定は任意です。 |
| Description | description
この設定は任意です。 |
| ID Number |
この設定は任意です。 |
| Language | preferredLanguage
この設定は任意です。 |
| Instructions |
その他のフィールドは、すべての認証方法で一般的なため、ここには記載しません。
高度なシナリオ
複数のLDAPサーバを使用する
Entering more than one name in the ldap_host_url field can provide some sort of resilience to your system. Simply use the syntax : ldap://my.first.server ; ldap://my.second.server ; ...
Of course, this will only work if all the servers share the same directory information, using a replication or synchronization mecanism once introduced in eDirectory and now generalized to the main LDAP-compatible directories.
There is one drawback in Moodle 1.5 - 1.6 implementation of LDAP authentication : the auth_ldap_connect() function processes the servers sequentially, not in a round robin mode. Thus, if the primary server fails, you will have to wait for the connection to time out before switching to the following one.
LDAPツリーで複数のユーザロケーション (コンテクスト) を使用する
There is no need to use multiple user locations if your directory tree is flat, i.e. if all user accounts reside in a ou=people,dc=my,dc=organization,dc=domain or ou=people,o=myorg container.
At the opposite, if you use the ACL mecanism to delegate user management, there are chances that your users will be stored in containers like ou=students,ou=dept1,o=myorg and ou=students,ou=dept2,o=myorg ...
Then there is an alternative :
- Look at the o=myorg level with the ldap_search_sub attribute set to yes.
- Set the ldap_context to ou=students,ou=dept1,o=myorg ; ou=students,ou=dept2,o=myorg.
Choosing between these two solutions supposes some sort of benchmarking, as the result depends heavily on the structure of your directory tree and on your LDAP software indexing capabilities. Simply note that there is a probability in such deep trees that two users share the same common name (cn), while having different distinguished names. Then only the second solution will have a deterministic result (returning allways the same user).
LDAPS (LDAP + SSL) を使用する
MSアクティブディレクトリ + SSL
If the Certificate Authority is not installed you'll have to install it first as follows:
- Click Start -> Control Panel -> Add or Remove programs.
- Click Add/Remove Windows Components and select Certificate Services.
- Follow the procedure provided to install the Certificate Authority. Enterprise level is a good choice.
Verify that SSL has been enabled on the server by installing suptools.msi from Windows installation cd's \Support\tools directory. After support tools installation:
- Select Start -> Run, write ldp in the Open field.
- From the ldp window select Connection -> Connect and supply valid hostname and port number 636. Also select the SSL check box.
If successful, you should get information about the connection.
Next step is to tell PHP's OpenLDAP extension to disable SSL certificate checking. On Windows servers you're most likely using pre-compiled PHP version, where you must create a path C:\OpenLDAP\sysconf. In this path create a file called "ldap.conf" with content:
TLS_REQCERT never.
Now you should be able to use ldaps:// when connecting to MS-AD.
付録
Child Domains and the Global Catalog in MS Active Directory
Moodle currently only has limited support for multiple domain controllers; specifically it expects each of the LDAP servers listed to contain identical sets of information. If you have users in multiple domains this presents an issue. One solution when working with MS-AD is to use the Global Catalog. The Global Catalog is designed to be a read-only, partial representation of an entire MS-AD forest, designed for searching the entire directory when the domain of the required object is not known.
For example your organisation has a main domain example.org, staff and students are contained in two child domains staff.example.org and students.example.org. The 3 domains (example.org, staff.example.org and students.example.org) each have a domain controller (dc01, dc02 and dc03 respectively.) Each domain controller contains a full, writable, representation of only the objects that belong to its domain. However, assuming that the Global Catalog has been enabled (see below) on one of the domain controllers (for example dc01) a query to the Global Catalog would reveal matching objects from all three domains. The Global Catalog is automatically maintained through replication across the active directory forest, it can also be enabled on multiple servers (if, for example, you need redundancy / load balancing.)
To make use of this in Moodle to allow logins from multiple domains is simple. The Global Catalog runs on port 3268 as opposed to 389 for standard LDAP queries. As a result, still assuming the Global Catalog is running on dc01, the 'ldap_host_url' would be ldap://dc01.example.org:3268. The rest of the settings are the same as for other MS-AS Auth setups.
You should use the 'ldap_contexts' setting to indicate the locations of individuals you wish to grant access. To extend the example above a little: In the example.org domain users are all in the 'Users' OU, in the staff.example.org domain users are in two OUs at the root of the domain, 'Support Staff' and 'Teaching Staff' , and in the students.example.org domain students are in an OU indicating the year that they enrolled, all of which are under the 'Students' OU. As a result our 'ldap_contexts' setting may look a little like this: 'OU=Users,DC=example,DC=org; OU=Support Staff,DC=staff,DC=example,DC=org; OU=Teaching Staff,DC=staff,DC=example,DC=org; OU=Students,DC=students,DC=example,DC=org.' The 'ldap_search_sub' option should be set to 'Yes' to allow moodle to search within the child OUs.
Its worth noting that the Global Catalog only contains a partial representation of the attributes of each object, as defined in the Partial Attribute Set supplied by Microsoft. However common information likely to be of use to a general Moodle installation (Forename, Surname, Email Address, sAMAccountName etc) is included in the set. For specific needs the schema can be altered to remove or add various attributes.
In most cases the Global Catalog is read-only, update queries must be made over the standard LDAP ports to the domain controller that holds the object in question (in our example, updating a student's details would require an LDAP query to the students.example.org domain controller - dc03, it would not be possible to update details by querying the Global Catalog.) The exception to this would be in an environment where there is only a single domain in the active directory forest; in this case the Global Catalog holds a writable full set of attributes for each object in the domain. However, for the purposes of Moodle authorisation, there would be no need to use the Global Catalog in this case.
Enabling the Global Catalog
The Global Catalog is available on Windows 2000 and Windows 2003 Active Directory servers. To enable, open the ‘Active Directory Sites and Services’ MMC (Microsoft Management Console) snap-in. Extend ‘Sites’ and then the name of the Site containing the active directory forest you wish to use. Expand the server you wish to enable the Global Catalog on, right click ‘NTDS settings’ and select the ‘Properties’ tab. To enable, simply click the ‘Global Catalog’ checkbox. Under a Windows 2000 server it is necessary to restart the server (although it won’t prompt you to); under Windows 2003 server it is not necessary to restart the server. In either case you will generally have to wait for the AD forest to replicate before the Global Catalog offers a representation of the entire AD forest. Changes made in Active Directory will also be subject to a short delay due to the latency involved with replication. If your AD servers are firewalled port 3268 will need to be opened for Global Catalog servers. If your organisation uses Microsoft Exchange then it its highly likely that at least one Domain Controller will already have Global Catalog enabled � Exchange 2000 and 2003 rely on the Global Catalog for address information, users also access the Global Catalog when using the GAL (Global Address List)
ldap auth_user_create() only suports Novell
After configuring user authentication with ldap I realized ldap only support edir (Novell) when combining ldap an email user confirmation. For example in my case (I use openldap) I have the following error after filling the user form:
auth: ldap auth_user_create() does not support selected usertype:"rfc2307" (..yet)
関連情報
- Using Moodle: User authentication forum
- Using Moodle PHP LDAP module does not seem to be present forum discussion
- LDAP enrolment