LDAP authentication: Difference between revisions
Helen Foster (talk | contribs) m (category edits) |
(A little bit more. Will I ever finish this? :-)) |
||
| Line 58: | Line 58: | ||
|- | |- | ||
| ldap_search_sub | | ldap_search_sub | ||
| | | If you have any sub organizational units (subcontexts) hanging from '''ou=moodleusers,dc=my,dc=organization,dc=domain''' and you want Moodle to search there too, set this to '''yes'''. Otherwise, set this to '''no'''. | ||
|- | |- | ||
| ldap_opt_deref | | ldap_opt_deref | ||
| | | Sometimes your LDAP server will tell you that the real value you are searching for is in fact in another part of the LDAP tree (this is called an alias). If you want Moodle to 'dereference' the alias and fetch the real value from the original location, set this to '''yes'''. If you don't want Moodle to dereference it, set this to '''no'''. If you are using MS-AD, set this to '''no'''. | ||
|- | |- | ||
| ldap_user_attribute | | ldap_user_attribute | ||
| | | The attribute used to name/search users in your LDAP tree. This option takes a default value based on the ''ldap_user_type'' value you choosed above. <u>So unless you need something special, you don't need to fill this in</u>. | ||
By the way, it's usually '''cn''' (Novell Edirectory and MS-AD) or '''uid''' (RFC-2037, RFC-2037bis and SAMBA 3.x LDAP extension), but if you are using MS-AD you could use '''sAMAccountName''' (the pre-Windows 2000 logon account name) if you need too. | |||
|- | |- | ||
| ldap_memberattribute | | ldap_memberattribute | ||
| | | The attribute used to list the members of a given group. This option takes a default value based on the ''ldap_user_type'' value you choosed above. <u>So unless you need something special, you don't need to fill this in.</u> | ||
By the way, the usual value is '''member'''. | |||
|- | |- | ||
| ldap_objectclass | | ldap_objectclass | ||
| | | The type of LDAP object used to search for users. This option takes a default value based on the ''ldap_user_type'' value you choosed above. <u>So unless you need something special, you don't need to fill this in.</u> | ||
Here are the default values for each of the ''ldap_user_type'' values: | |||
* '''User''' for Novel Edirectory | |||
* '''posixAccount''' for RFC-2037 and RFC-2037bis | |||
* '''sambaSamAccount''' for SAMBA 3.0.x LDAP extension | |||
* '''user''' for MS-AD | |||
|- | |- | ||
| Force change password | | Force change password | ||
| Line 97: | Line 107: | ||
|- | |- | ||
| ldap_creators | | ldap_creators | ||
| | |||
|- | |||
| First name | |||
| | |||
|- | |||
| Surname | |||
| | |||
|- | |||
| Email address | |||
| | |||
|- | |||
| | |||
| | |||
|- | |||
| | |||
| | |||
|- | |||
| | |||
| | |||
|- | |||
| | |||
| | |||
|- | |||
| | |||
| | |||
|- | |||
| | |||
| | |||
|- | |||
| | |||
| | |||
|- | |||
| | |||
| | |||
|- | |||
| | |||
| | |||
|- | |||
| | |||
| | |||
|- | |||
| | |||
| | |||
|- | |||
| | |||
| | | | ||
|- | |- | ||
Revision as of 22:48, 18 February 2006
This document describes how to set up LDAP authentication in Moodle. You can find a Basic Scenario, where everything is simple and straightforward, and that should be enough for most installations. If your installation is a little bigger and you are using multiple LDAP servers, or multiple locations (contexts) for your users in your LDAP tree, then have a look at the Advanced Scenarios.
Basic Scenario
Assumptions
- Your Moodle site is located at http://your.moodle.site/
- You have configured your PHP installation with the LDAP extension. It is loaded and activated, and it shows when you go to http://your.moodle.site/admin/phpinfo.php (logged in as user 'admin').
- Your LDAP server has 192.168.1.100 as its IP address.
- You are not using LDAP with SSL (also known as LDAPS) in your settings. This might prevent certain operations from working (e.g., you cannot update data if you are using MS Active Directory -- MS-AD from here on --), but should be OK if you just want to authenticate your users.
- You are using a single domain as the source of your authentication data in case you are using MS-AD (more on this in the Appendices).
- You are using a top level distinguished name (DN) of dc=my,dc=organization,dc=domain as the root of your LDAP tree.
- You have a non-privileged LDAP user account you will use to bind to the LDAP server. This is not necessary with certain LDAP servers, but MS-AD requires this and it won't hurt if you use it even if your LDAP server doesn't need it. Make sure this account and its password don't expire, and make this password as strong as possible. Remember you only need to type this password once, when configuring Moodle, so don't be afraid of making it as hard to guess as possible. Let's say this user account has a DN of cn=ldap-user,dc=my,dc=organization,dc=domain, and password hardtoguesspassword.
- All of your Moodle users are in an organizational unit (OU) called moodleusers, which is right under you LDAP root. That OU has a DN of ou=moodleusers,dc=my,dc=organization,dc=domain.
- You don't want your LDAP users' passwords to be stored in Moodle at all.
Configuring Moodle authentication
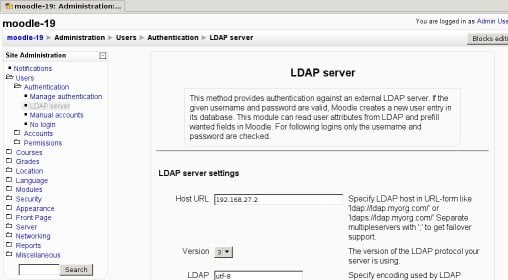
Log in as an admin user and go to Administration >> Users >> Authentication. In the drop down listbox titled "Choose an authentication method" select "Use an LDAP Server". You will get a page similar to this one:
Now, you just have to fill in the values. Let's go step by step.
| Field name | Value to fill in |
|---|---|
| ldap_host_url | As the IP of your LDAP server is 192.168.1.100, type "ldap://192.168.1.100" (without the quotes). |
| ldap_version | Unless you are using a really old LDAP server, version 3 is the one you should choose. |
| ldap_preventpassindb | As you don't want to store the users's password in Moodle's database, choose Yes here. |
| ldap_bind_dn | This is the distinguished name of the bind user defined above. Just type "cn=ldap-user,dc=my,dc=organization,dc=domain" (without the quotes). |
| ldap_bind_pw | This is the bind user password defined above. Type "hardtoguesspassword" (without the quotes). |
| ldap_user_type | Choose:
|
| ldap_contexts | The DN of the context (container) where all of your Moodle users are found. Type ou=moodleusers,dc=my,dc=organization,dc=domain here. |
| ldap_search_sub | If you have any sub organizational units (subcontexts) hanging from ou=moodleusers,dc=my,dc=organization,dc=domain and you want Moodle to search there too, set this to yes. Otherwise, set this to no. |
| ldap_opt_deref | Sometimes your LDAP server will tell you that the real value you are searching for is in fact in another part of the LDAP tree (this is called an alias). If you want Moodle to 'dereference' the alias and fetch the real value from the original location, set this to yes. If you don't want Moodle to dereference it, set this to no. If you are using MS-AD, set this to no. |
| ldap_user_attribute | The attribute used to name/search users in your LDAP tree. This option takes a default value based on the ldap_user_type value you choosed above. So unless you need something special, you don't need to fill this in.
By the way, it's usually cn (Novell Edirectory and MS-AD) or uid (RFC-2037, RFC-2037bis and SAMBA 3.x LDAP extension), but if you are using MS-AD you could use sAMAccountName (the pre-Windows 2000 logon account name) if you need too. |
| ldap_memberattribute | The attribute used to list the members of a given group. This option takes a default value based on the ldap_user_type value you choosed above. So unless you need something special, you don't need to fill this in.
By the way, the usual value is member. |
| ldap_objectclass | The type of LDAP object used to search for users. This option takes a default value based on the ldap_user_type value you choosed above. So unless you need something special, you don't need to fill this in.
Here are the default values for each of the ldap_user_type values:
|
| Force change password | |
| Use standard Change Password Page | |
| ldap_expiration | |
| ldap_expiration_warning | |
| ldap_exprireattr | |
| ldap_gracelogins | |
| ldap_graceattr | |
| ldap_create_context | |
| ldap_creators | |
| First name | |
| Surname | |
| Email address | |
Advanced Scenarios
Using multiple LDAP Servers
Using multiple user locations (contexts) in your LDAP tree
Appendices
Talk about Global Catalog servers and MS Active Directory.