External services security
Moodle 2.0
Descriptions of security framework for web services, also used for RSS feeds, embedded application and similar parts that can not use normal HTTP cookies.
Overview
Current solutions:
- user keys for gradebook import and export - see require_user_key_login() and db table user_private_key
- open RSS feeds - no security at all
- chat_sid tokens - generated separately for each user in each chat
- calendar export - hash from user name, password and salt
- hacky cookie emulation in visual gradebook plugin
Design
Different uses
The external API may be used from different places:
- directly from PHP - no authentication, current user session is used ($USER, $SESSION)
- simple web service layer - easy to use and setup WS layer designed for interaction with enterprise systems (each having own single purpose user account), the protocol is stateless, username and password is sent with each request; security is enforced on multiple levels
- full WS layer with token authentication - it is more flexible and enables normal users to use some restricted parts of the WS APIs, performance might be significantly improved by emulation of sessions
- when embedding external applications - external application receives unique token which is used instead of normal browser session cookie, the session is linked to the current user session in browser, the token is automatically invalidated after logout
- RSS feeds, iCals, etc. - token login, no permanent session
API layers
Three layers:
- external server interface (SOAP, REST, RSS, etc.) - deals with tokens, emulates user session, parameter processing
- public PHP API - functions usable directly from PHP, list generated from inline PHP docs, need to verify all parameters and access control, may access $USER, should not manipulate $SESSION directly, must not read $_POST or $_GET
- low level internal API - as fast as possible, basic param validation, no access control, must not touch $USER, $SESSION, $_GET or $_POST, must not use has_capability() or require_login()!
Context restrictions
Context restriction of token validity should be effective against security problems in external applications interacting with Moodle. Some external applications do not have any access to http cookies, solution is to create temporary tokens. Context restrictions would allow us to grant external access to individual activities, courses ,etc..
Implementation
PHP API
This simplest case of using the external API. The calling call has to make sure the current $USER and $SESSION is valid. Optionally the caller may set up the context restriction manually. This should be the easiest way to start with Moodle modifications and integration with other PHP software.
Simplified web services
This type of web service is using simple username+password authentication (in future could be username+certificate). The communication integrity/privacy can be protected using https. Each external application is using own user account. These user accounts can not be used for normal login into moodle vie web interface.
This type of WS is intended primarily for integration with student information systems or other enterprise software.
webservice auth plugin
It is recommended to create separate user for each external application. The benefit of this auth type is that it can not be used for normal log-in from the web interface.
Several people questioned the security of sending username+password with each request - it is not a problem because this password is used only for web services, it can not be used for anything else. This means that the password is effectively a standard authentication token ;-) We coudl replace this password by a public certificate stored in the user profile field.
WS entry point
Separate php file /webservice/xxx/simpleserver.php
external_services_users table
Specifies which user may use each external service when restrictedusers flag set in service.
| Field | Type | Default | Description |
|---|---|---|---|
| id | int(10) | auto-incrementing | |
| externalserviceid | int(10) | foreign key, reference external_services.id | |
| userid | int(10) | foreign key, reference user.id | |
| iprestriction | varchar(255) | NULL | restrict access to some ips or subnets only |
| validuntil | int(10) | NULL | invalidate after (once the date is reached the user cannot access the service) |
| timecreated | int(10) | time when this record added (date of the user/service relation creation) |
Steps needed to configure simple web service access
- enable web services
- create new service in some local plug-ip (add code into /local/yourplugin/db/services.php) or manually add new service with some functions
- add new user, set auth plugin to webservice (normal add user UI)
- enable web service layer plugin (admin UI)
- optionally add user into list of users that are allowed to use specific external services (admin UI)
- set up user permissions needed in function implementations. All required capabilities should be listed in the external function description.
- set up permission to use specific web services (optional, services do not need to specify required capability)
- Log as admin
- Add a new user
- Enable the Web Service Authentication plugin
- In the new user profil, change authentication method for web services
- In advance feature, enable web services
- In Plugin/Web Services/Manage protocol, enable the protocol you need
- In Plugin/Web Services/External Services, Add a new service, activate it and add some function to this service.
- If the selected service has restricted user option activated, assign the new user to this service
- If the selected service has required capability, assign this capability to the new user
- Assign the capability to use the selected protocol - you'll probably want to create a Web Service role for that
- the new user can now access web service from the enabled protocol with his username/password
General web services
More flexible than the WS with simplified authentication and setup. The performance may be significantly improved by emulation of sessions. The authentication is based on security tokens (user, context and purpose specific) that are generated in normal Moodle interface and then used in other external applications that are using our web services. This allows us to give only partial access to some parts of WS api, external applications and services do not need to be fully trusted.
The main drawback is that the complex configuration does not encourage admins to keep everything secured.
external_tokens
Stores permanent tokens for cookieless access, script runs without real session. (Later might have to add emulated session for performance reasons.)
| Field | Type | Default | Description |
|---|---|---|---|
| id | int(10) | auto-incrementing | |
| token | varchar(128) | private access key value | |
| tokentype | int(3) | type of token: 0=permanent, no session; 1=linked to current browser session via sid; 2=permanent, with emulated session | |
| userid | int(10) | foreign key, references user.id | |
| creatorid | int(10) | the token creator (an administrator) | foreign key, references user.id |
| externalserviceid | int(10) | foreign key, references external_services.id | |
| sid | varchar(128) | NULL | links to browser or emulated session |
| contextid | int(10) | security restriction, token usable only in this context, references context.id | |
| iprestriction | varchar(255) | NULL | IP address restriction, list of allowed addresses |
| validuntil | int(10) | NULL | timestampt - valid until date |
| timecreated | int(10) | time when key created | |
| lastaccess | int(10) | time when key last used for access |
Steps needed to configure general web service access
- enable general web services - global switch affecting all general web services (admin UI)
- enable web service layer plugins (admin UI)
- setup user permission which allows them to create tokens in some specific context for some specific purpose (roles UI)
- set up user permissions needed in function implementations
- set up permission to use specific web services (optional, services do not need to specify required capability)
- each user must create permanent token in specific context for specific purpose (user UI)
- user must copy/past this token to external application
Random all-time valid token
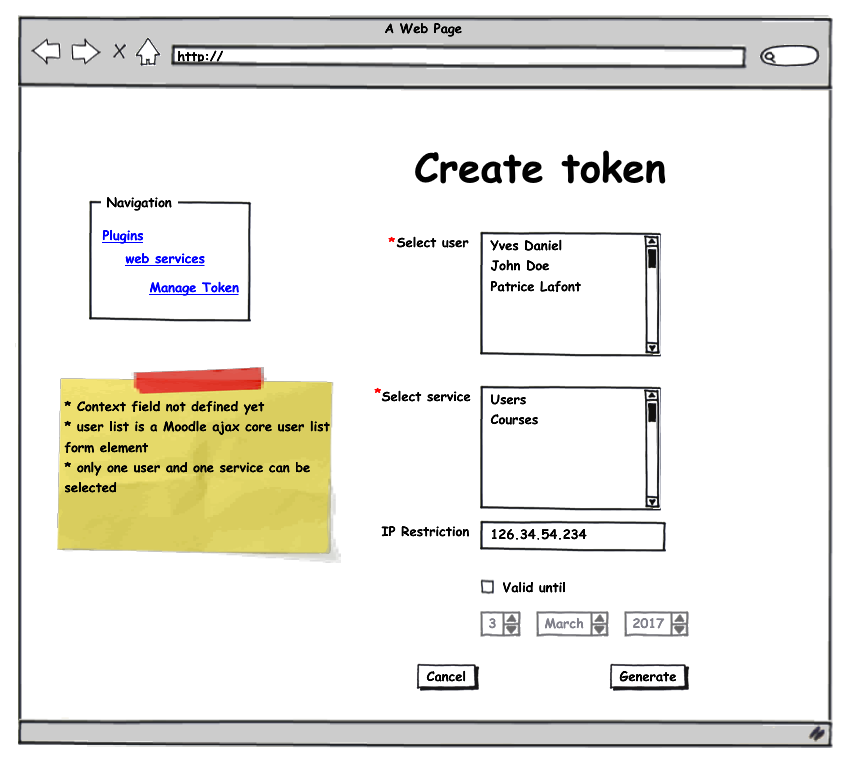
A user can use the same token to call a web service. We call this token an all-time valid token.
Specificity
- A token can be created by a Moodle administrator (administration page) or a simple Moodle user (user profil).
- An administrator has the ability to create a token for another Moodle user but not for himself neither for another administrator (for security purpose).
- A token is always linked to a Moodle user.
- A token cannot be linked to an administrator .
- A Moodle user create his own token on his profil page.
- To create a token, a user need "moodle/webservice:createtoken" capability.
- An administrator create token for other on a web service token page.
- An administrator cannot see token that he didn't create.
- A token is generated randomly and is long enough.
- A token can be used by an external web application. (by browser)
- A token can be used by a mobile application. (i.e. iphone native application)
- A token is sent by the external application at the same time that the function parameters are sent.
- When the user create a token, he must select a service (to link the token to a service). Only services that the user has capability on are displayed.
- ip restriction and valid until fields are optional.
- A Moodle user must select an aera on which the token can be valid. (course, ...) - TBD - unclear yet
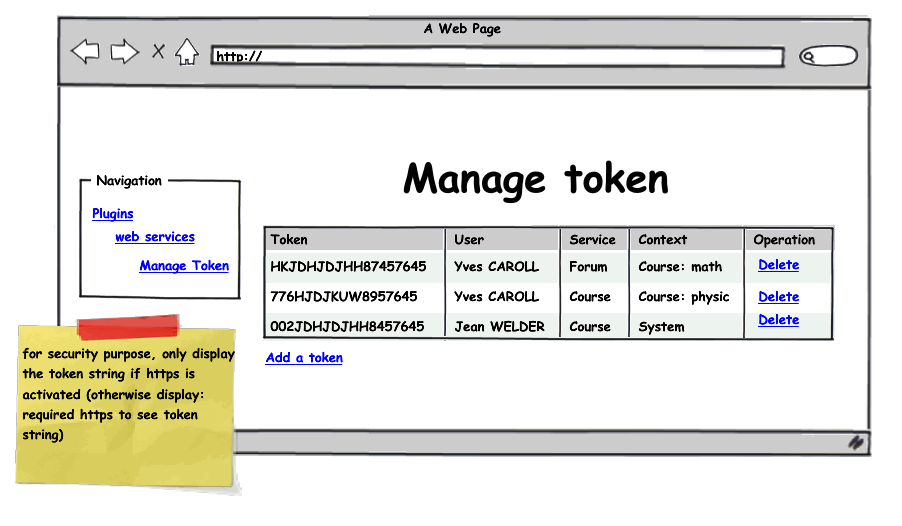
- A user can only see token string if https is enabled.
- A token can be linked to only one service.
Administration: token management (valid until field is missing here):
Application embedding
Similar to general WS, the token is linked to current session - when user logs out, the external token is immediately invalidated. The administration is much easier and the tokens are usually created automatically.
The external applications maybe be embedded into browser or they can be launched as separate programs (ex.: Java Web Start, Flex, external media players, etc.)
It is not necessary to use WS layers defined in /webservices/xxx/, the same infrastructure may be used in all ajax scripts that do not have access to browser cookies.
RSS, iCALs and other feeds
All cookie-less scripts such as RSS can use the external API and together with the permanent tokens. In fact ATOM is a nice example of RESTful protocol :-)